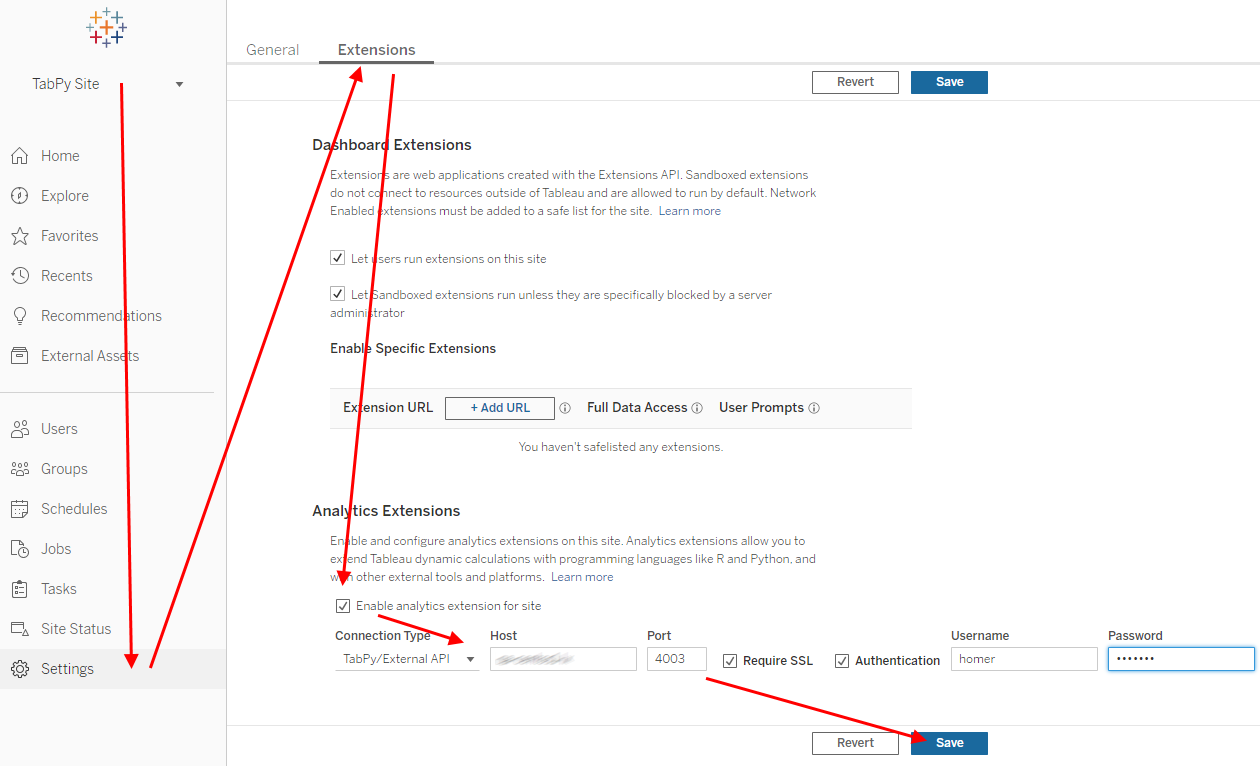
Intro
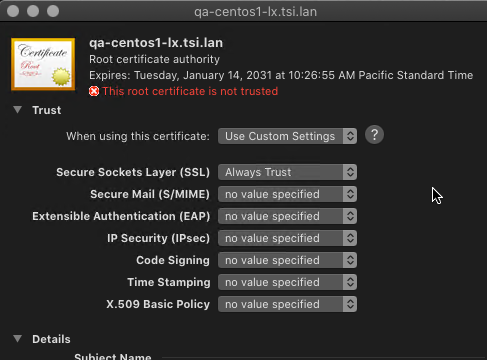
When running Tableau Server on Linux and need it to connect to secure TabPy or secure Rserve instances (or any other analytics extension over secured channel) for Tableau Server to trust the connection it need to know to trust the certificate analytics extension is using. Some more details about Tableau and trusted certificates are in this post – Tableau and Trusted Certificates for Analytics Extensions.
In this post, I will show you how to install a trusted certificate (root or self-signed certificate) on Linux. Remember Rserve sends to Tableau leave certificate only so you may need to install the whole chain as trusted certificates.
NOTE: Instructions below may not work for your specific Linux version – check with documentation for your exact system.
Certificate formats: PEM, DER, PFX, etc.
There are a few different formats certificate file can be stored in. For the instructions below only PEM and DER are used. Some details about specific formats and how they are related can be found at https://aboutssl.org/cer-vs-crt/.
PEM and DER are just different encoding for the same data. DER is binary and PEM is Base64 encoded DER.
One format can be converted to another with OpenSSL. E.g. to convert DER to PEM run
openssl x509 -inform der -in cert.der -out cert.pemMore examples for how to convert certificate commands are at https://aboutssl.org/ssl-tools/ssl-converter.php.
NOTE: you only need certificates (public part) and not private key for it.
RPM-based Linux Steps
The following are the instructions for RPM-based Linux (CentOS, Fedora, Red Hat, etc.).
Copy PEM certificate to /etc/pki/ca-trust/source/anchors:
sudo cp cert.pem /etc/pki/ca-trust/source/anchors/cert.pemRun the following command:
sudo update-ca-trustFor the certificate to be picked up by Tableau Server it is recommended to restart the whole machine. Restarting just Tableau Server may work as well but is not guaranteed.
Debian-based Linux Steps
For Debian-based Linux (Debian, Ubuntu, Kubuntu, etc.) use PEM certificate in .crt file. It means the format for the certificate file is PEM, but the file extension is required to be .crt.
First copy certificate file to /usr/local/share/ca-certificates:
sudo cp cert.crt /usr/local/share/ca-certificates/cert.crNow run the following command:
sudo update-ca-certificatesFor the certificate to be picked up by Tableau Server it is recommended to restart the whole machine. Restarting just Tableau Server may work as well but is not guaranteed.
Additional reading
Related posts: